Our apps are safe from CVE-2019-13013
28/08/19 12:48
First off, we have to give a HUGE thank you to Obdev (they make Little Snitch) for both finding this and informing us before making this public. Here is their post on the issue: The story behind CVE-2019-13013
About a month or so ago, we got an email from Obdev informing us that they had discovered a vulnerability (CVE-2019-13013) in macOS apps that use a privileged helper tool. These tools are usually used to separate code/tasks that require admin privileges. The tools get installed using a function called SMJobBless() and go into /Library/PrivilegedHelperTools and when launched have the ability to do things at an admin level without having to ask the user for their password each time.
For example, here's what that folder would contain:
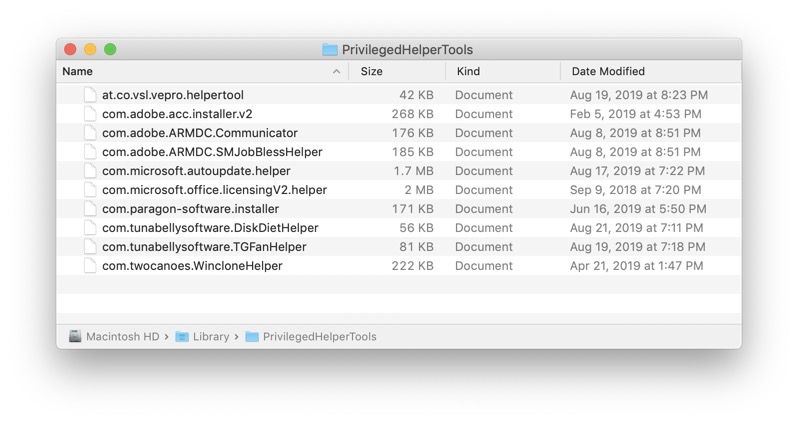
com.tunabellysoftware.DiskDietHelper is for Disk Diet
com.tunablelysoftware.TGFanHelper is for TG Pro.
The way the documentation from Apple is written, it would appear that when installing a helper tool with SMJobBless(), only the app installing it can interact with it. However Obdev discovered this is not the case! Any app with the correct code can interact with the helper tools and get them to do things that weren't expected.
Here's the old work flow for TG Pro and its helper tool before the fix:
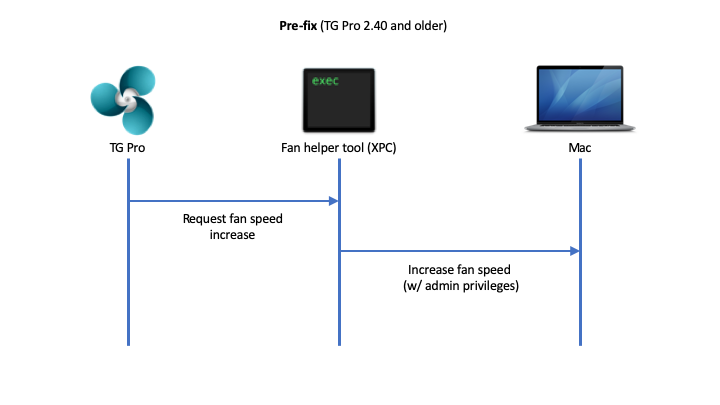
There was no validation between the app and the helper tool since it was assumed from the documentation that only TG Pro could communicate with it.
To fix this, the helper tool now verifies that the calling application is actually TG Pro. It does this by verifying the code signing signature of the calling app, since this cannot be forged or changed. This ensures that if another app tries to communicate with the helper tool, the XPC connection will be denied.
Here is the workflow in TG Pro 2.42 and higher after the fix:
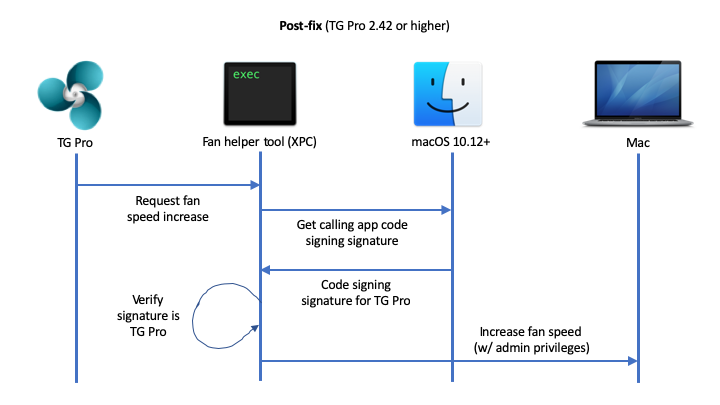
Please note that in the diagram it shows macOS 10.12+. This is due to the fact that the required functions for validating the calling app over XPC were only added in 10.12. To ensure that the fix is active, make sure to have this or a higher version of macOS installed. Users are still able to install TG Pro 2.42 on 10.10 or higher so they continue to get the other fixes in the updates, although it will not have the fix for this potential privilege escalation.
About a month or so ago, we got an email from Obdev informing us that they had discovered a vulnerability (CVE-2019-13013) in macOS apps that use a privileged helper tool. These tools are usually used to separate code/tasks that require admin privileges. The tools get installed using a function called SMJobBless() and go into /Library/PrivilegedHelperTools and when launched have the ability to do things at an admin level without having to ask the user for their password each time.
For example, here's what that folder would contain:

com.tunabellysoftware.DiskDietHelper is for Disk Diet
com.tunablelysoftware.TGFanHelper is for TG Pro.
The way the documentation from Apple is written, it would appear that when installing a helper tool with SMJobBless(), only the app installing it can interact with it. However Obdev discovered this is not the case! Any app with the correct code can interact with the helper tools and get them to do things that weren't expected.
Here's the old work flow for TG Pro and its helper tool before the fix:

There was no validation between the app and the helper tool since it was assumed from the documentation that only TG Pro could communicate with it.
To fix this, the helper tool now verifies that the calling application is actually TG Pro. It does this by verifying the code signing signature of the calling app, since this cannot be forged or changed. This ensures that if another app tries to communicate with the helper tool, the XPC connection will be denied.
Here is the workflow in TG Pro 2.42 and higher after the fix:

Please note that in the diagram it shows macOS 10.12+. This is due to the fact that the required functions for validating the calling app over XPC were only added in 10.12. To ensure that the fix is active, make sure to have this or a higher version of macOS installed. Users are still able to install TG Pro 2.42 on 10.10 or higher so they continue to get the other fixes in the updates, although it will not have the fix for this potential privilege escalation.
blog comments powered by Disqus
